The Hidden Compliance Problem with Enterprise Software Pipelines
)
Pipeline Compliance at Scale is Tough
September 10, 2025
Modern enterprise organizations run on code - from software automation to deploying infrastructure and even HR systems. For global organizations, it’s not unusual to have 10,000 or more source code repositories, each with multiple workflows for CI/CD and other automations. That scale creates a massive compliance challenge: how do you ensure that every pipeline consistently follows corporate security policies, prevents vulnerabilities from slipping through, and produces auditable evidence for regulators?
The stakes are deceptively high.
Insecure or non-compliant pipelines can cause financial losses, client data exposure, or damage to brand reputation to name a few negative impacts. At scale, its incredibly difficult to monitor the tens (sometimes hundreds) of thousands of pipelines within your organization. You must monitor for adherence to corporate governance, internal security policies, compliance frameworks such as SOC2, runner configurations — the list goes on and on.
A break in any one of those could expose your organization to harm. And unlike traditional infrastructure, pipelines are dynamic. New repositories are created daily. Pipelines are stored in code, so any developer with access can make modifications. Old pipelines don't receive security updates. Corporate governance and security policies are updated and developers (with little to no experience in corporate governance) are tasked with remediating them.
Traditionally, large enterprises have attempted to address this problem with centralized scanning platforms, policy-as-code frameworks like OPA, hardened runners, and SBOM mandates. While these are necessary steps, they are also time-consuming, expensive, and siloed. Security and platform teams spend countless hours stitching together tools, building dashboards in Splunk or Grafana, and chasing down non-compliant repos. The result is often a lagging view of compliance health rather than the real-time visibility leaders need. Exceptions pile up, evidence becomes fragmented, and executives are left with metrics that reflect yesterday’s state — not today’s risk.
That’s why CodeCargo is introducing Compliance Guardrails.
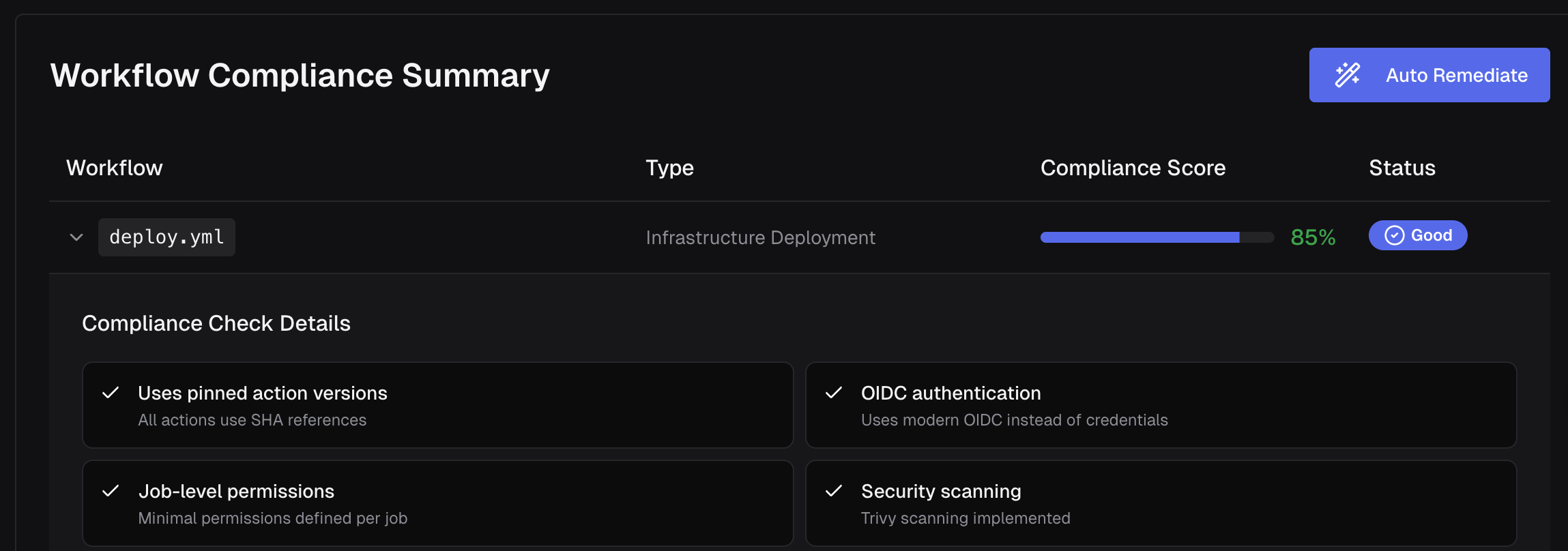
Instead of burdening security and platform teams with endless policy rewrites, dashboard maintenance, and manual enforcement, Compliance Guardrails use our agentic capability to interpret OPA rego, SBOM requirements, and even corporate compliance documents into clear, actionable natural language for developers. Guardrails don’t just surface issues — they apply rules from OPA and your compliance frameworks directly against CI/CD workflows. This ensures that every pipeline is continuously evaluated on every single Git commit and compliant by design. Non-compliant evidence is logged and centralized automatically.
The result is continuous assurance across thousands of repos — without the cost, silos, and complexity of today’s compliance tooling. Enterprises can stay secure and auditable while developers keep shipping.
C
CodeCargo Team
The CodeCargo team writes about GitHub workflow automation, developer productivity, and DevOps best practices.
)