Changing the Paradigm: Workflow Compliance at Scale with CodeCargo
)
Enterprise Scale Workflow Guardrails are Here
October 29, 2025
Today we are excited to announce CodeCargo's workflow guardrails feature! With CodeCargo, you can now apply security, best-practices, and compliance guardrails at scale to your GitHub Actions Workflows. CodeCargo will evaluate every single workflow in your GitHub organization to ensure they meet your enterprise requirements and provide not only alerts, but remediations to make sure everything works as intended.
What are Compliance Guardrails?
In my previous DevOps consulting position, I helped many companies develop their automation standards and compliance documents. The documents were designed to help keep enterprise organizations safe by creating a set of standards that apply to automations. For example, they generally included best-practices such as "GitHub Actions should reference explicit SHA hashes" and "run Terraform Plan before Terraform Apply."
The biggest issue with these documents is a centralized team (such as cloud security or cloud center of excellence) would own them but developers would have to ensure their automations actually followed the recommendations.
These issues presented themselves as information and implementation gaps.
SWE teams struggle to implement the proper controls to ensure their workflows were compliant. Even if they could implement them correctly, there is no way to actually test this. Centralized security/CCoE teams are unable to get a good view of automation compliance at scale for hundreds or thousands of pipelines. This leads to CXOs never having the proper information to make decisions to protect both the company and their customers.
Today that changes.
How it Works
After you create your CodeCargo account, the platform will run a "compliance guardrails" check against every single workflow in your GitHub organization. This check will evaluate each workflow against a series of "compliance guardrail rules." Here is an example rule:
Every GitHub Actions Workflow must explicitly define minimum required permissions for GITHUB_TOKEN at the workflow job level. Default permissions or "write-all" violate least privilege principle.
Compliance guardrail rules are evaluated via a combination of declarative code, GenAI, and tool calls to ensure accuracy. The platform then provides two distinct views of evaluated workflows: one designed for developers and the other defined for compliance teams.
CodeCargo will re-evaluate any GitHub Workflow that has been modified as part of an approved Pull Request to ensure that new versions remain compliant.
Technical / SWE View
For a technical view of each workflow's evaluation, navigate to the Project where your workflow is defined. Then click the "Guardrails" tab near the top of the page. This dashboard will show the evaluation scorecard for every single GitHub Workflow in this project. Each GitHub Actions Workflow is given a compliance score:
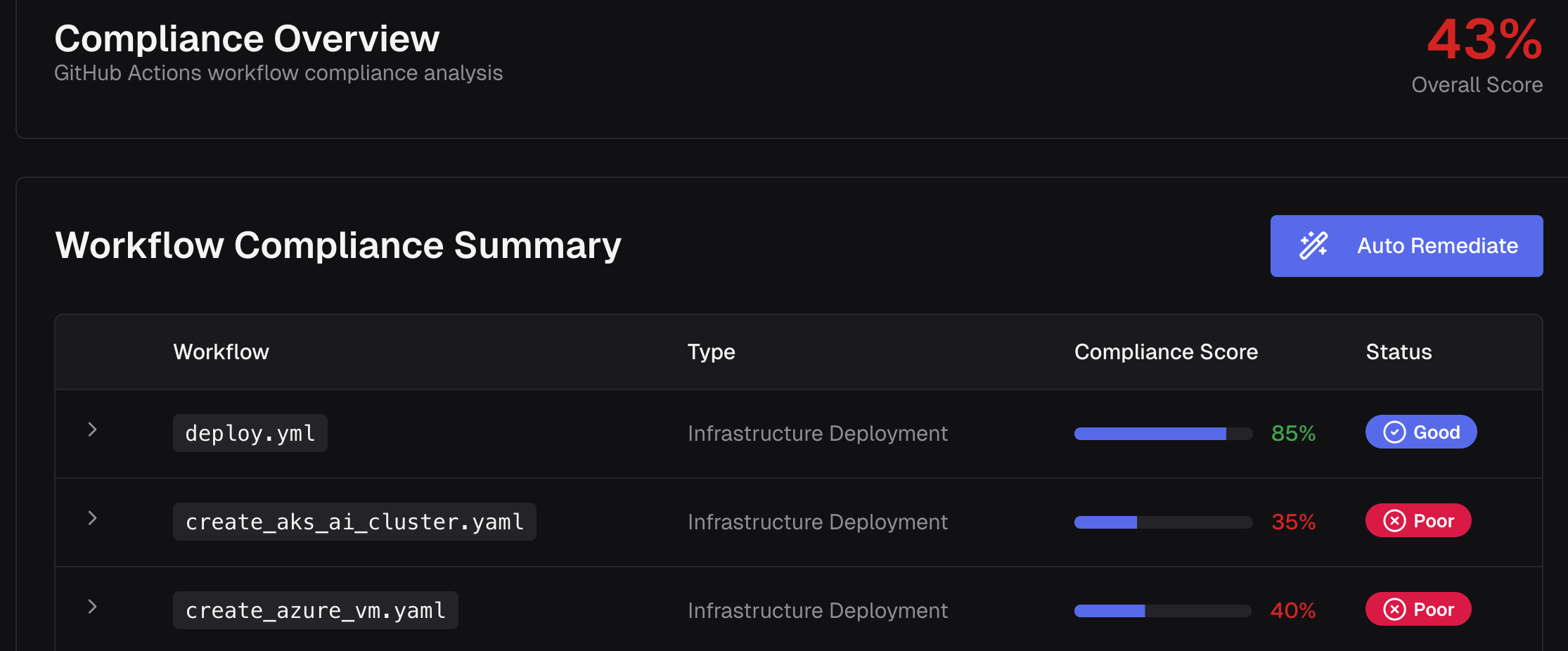
passed rules / total rules) and a listing of each applicable rule and whether the workflow passed or failed that rule. CodeCargo will only evaluate guardrail rules that "make sense" - that is, ones that apply to the workflow in a logical manner. For example, you might have a rule that specifies the workflow must run
Terraform Plan before Terraform Apply. This rule will only be evaluated if the GitHub Workflow actually executes Terraform code.If you click on a single workflow, the dashboard will expand to show you all of the applicable rules that were used to evaluate that workflow's compliance score in addition to which ones were PASS / FAIL.
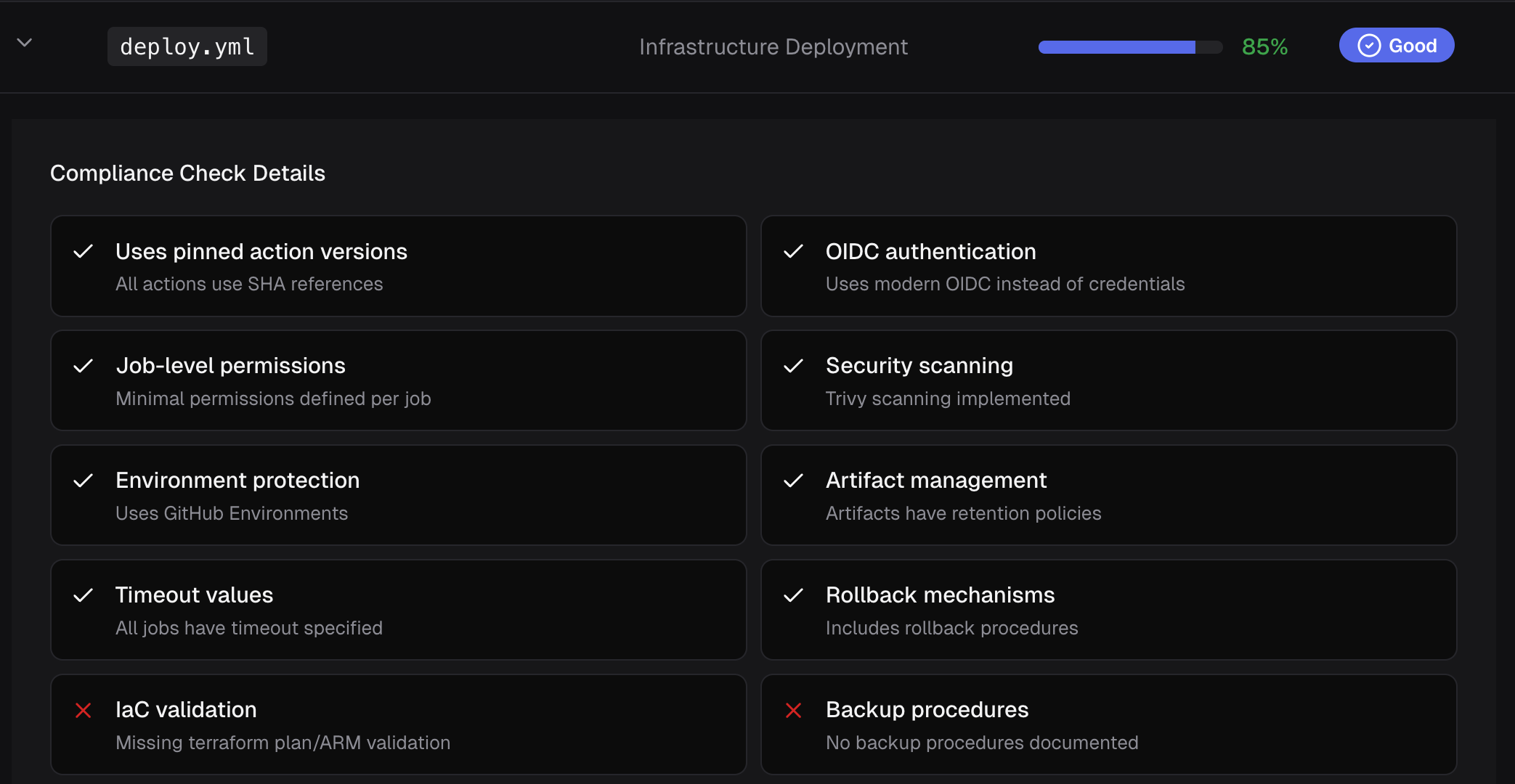
This dashboard gives developers the information they need to ensure their workflows remain compliant. Our platform helps the developer implement fixes to the workflows in two key ways:
- CodeCargo's Expert Workflow Agent can automatically implement code changes and create PRs to remediate issues discovered during compliance checks
- CodeCargo can create GitHub Issues for each enhancement
In addition, developers can simply copy/paste the failed rules into GitHub Copilot (or their favorite GenAI tool of choice) and ask it to implement the change. Once the developer creates and approves a PR with the enhancements, CodeCargo will re-evaluate the workflow to ensure everything is in good shape.
Global View
CodeCargo administrators are able to see a global view of all compliance guardrail evaluations. This dashboard shows a global average compliance score for every GitHub Workflow in your organization, score over time, and a listing of the current compliance guardrail rules.
This provides actionable intelligence to your compliance team to ensure they have the tools necessary to protect enterprise organizations from a large range of potential security or policy (e.g. SOC2, GDPR) violations. Here is a screenshot of the administrator view:
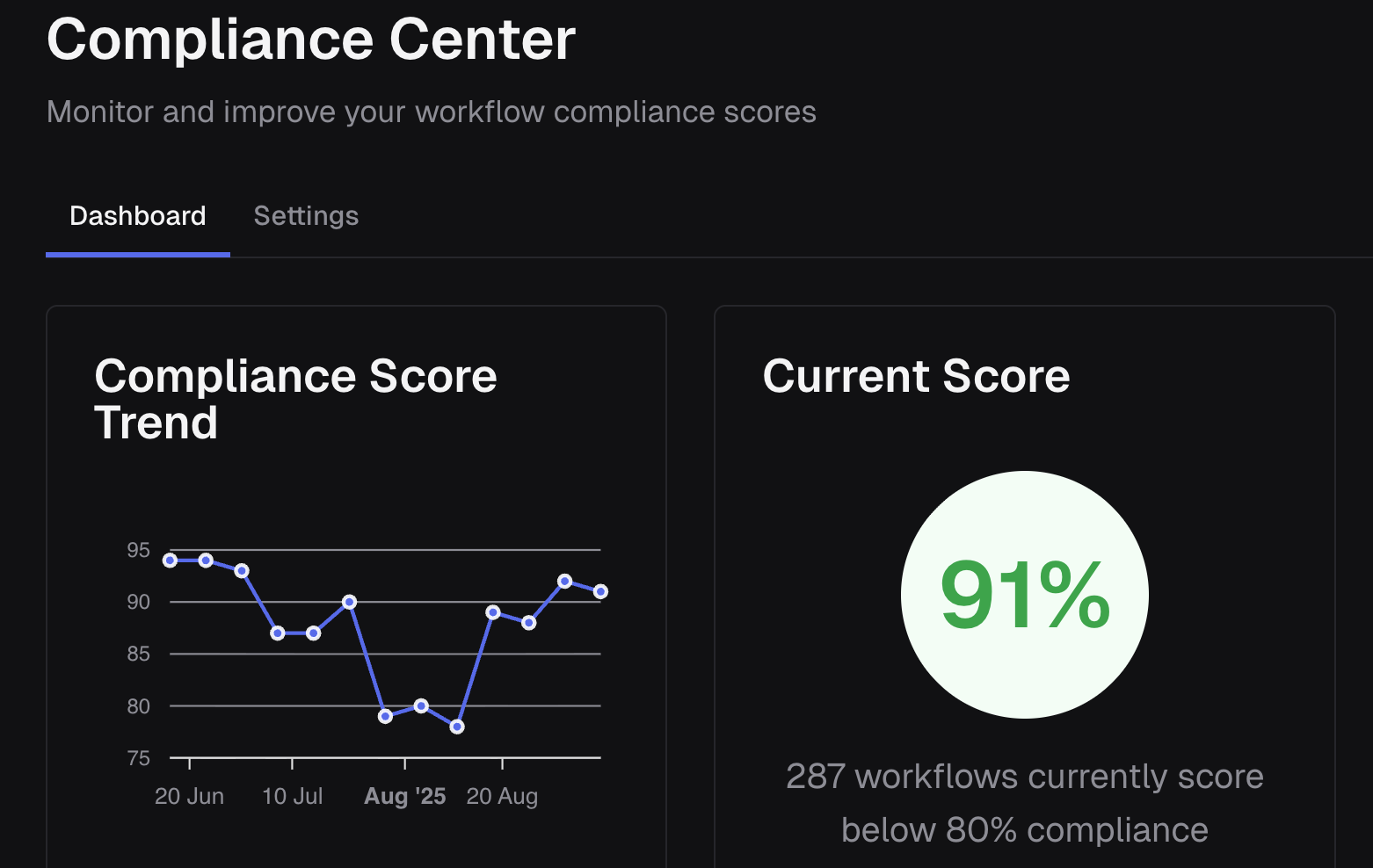
Administrators can track these scores over time as a KPI for engineering organizations.
Benefits of Evaluation "at Scale"
Pretty much every single GenAI inference provider can evaluate a single GitHub Workflow for generic best-practices compliance. However, enterprise organizations typically have hundreds, thousands, or even tens-of-thousands of workflows in their GitHub estate. Publishing corporate guidance that instructs individual SWEs to evaluate their workflows against compliance standards is not practical for modern organizations.
Today, organizations must provide the workflow compliance and best-practices specification to individual developers. Then those developers must read the 50+ page document, understand which rules apply, and implement fixes. Once the fixes are implemented, nobody will actually be able to track that the workflow is in compliance, and if the workflow needs to be modified in the future, nobody will know if the new workflow remains compliant.
CodeCargo provides this at scale, for every single workflow in your GitHub Organization, automatically. You'll not only gain low-level tactical detail about each workflow (and how to implement fixes), but you can see a global view to understand how well your organization is doing at large. This actionable intelligence allows your organization to proactively identify risks before there is an impact and safeguard your corporate and customer information.
C
CodeCargo Team
The CodeCargo team writes about GitHub workflow automation, developer productivity, and DevOps best practices.
)